World’s largest 3D printer can print a house in under 80 hours
The University of Maine just revealed the world’s largest 3D printer, and it is an absolute beast. The printer, which the university named Factory of …
The University of Maine just revealed the world’s largest 3D printer, and it is an absolute beast. The printer, which the university named Factory of …

There were plenty of reasons to get excited about Deadpool & Wolverine, but now we have one more, as a prolific leaker has teased an …

Remember all the dismissiveness and whispers that were prevalent back in the early days of Apple TV+? There was a time, for example, when the …

While the Apple Card has been in people’s wallets for a few years now, the company has done a pretty terrible job at marketing where …

Done with Fallout and looking for something new to binge? This Thursday, Netflix unleashed all eight episodes of its new supernatural dramedy series Dead Boy …

Researchers may have found a realistic alternative to plastic. The alternative comes in the form of a newly developed “bioplastic” pellet, which could prove to …

Apple is expected to announce a new iPad Pro on May 7. After a mild M2 update in late 2022, rumors indicate a significant refresh …

Netflix has a mixed track record, to say the least, when it comes to original movies. It’s poured serious money into chasing a Best Picture …

For the past five years, the Epic Games Store has been giving away free PC games each and every week. If you’re looking to boost your …
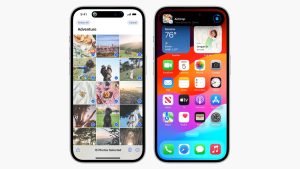
iOS 17 is Apple‘s current operating system for its iPhone models. Announced during the WWDC 2023 keynote, the Cupertino firm focused on three main features: …

Where can you get the best tech deals online? Look no further, because there are so many incredible sales available to shop. Our expert commerce …

Remember the good old days when you could escape from a never-ending meeting by simply leaving your laptop behind? “Hey guys, I have to get …

You don’t have to read our guide on the best Sony headphones and earbuds to know that Sony is a leader in the headphones market. …

By Kirstie McDermott Remote work triumphed during the pandemic, but in the time since, tech firms have been shepherding their staff back into the office. …

tvOS 18 is Apple’s upcoming new operating system for the Apple TV streaming media player and HomePod speakers. After a packed tvOS 17 update, it’s …

I have owned an iPhone for almost half of my life. Still, I don’t think I actually knew how to correctly type on my device …

There are some great sales happening on Thursday, like an exclusive deal that gets you the powerful and compact GEEKOM Mini IT11 mini PC for …

With Qi2 wireless charging standard now available, Satechi is the latest accessory maker to announce new products that can wirelessly charge your iPhone twice as …

iPadOS 18 is Apple’s upcoming operating system for its iPad models. After offering a few design changes and focusing on health with iPadOS 17, Apple …

This is a sponsored article. All content and opinions expressed within are of the author. BGR has covered several impressive GEEKOM deals over the past …

Giancarlo Esposito’s gritty new crime drama Parish, in which he plays a former wheelman who went straight and started a family, has reminded me how …

Earlier this month, display analyst Ross Young said that Apple was preparing to add a miniLED display to the upcoming 12.9-inch iPad Air. According to …

If you have an Amazon Prime subscription, you also have access to the Prime Video streaming service. If you have Prime Video, there are a …

No matter how confident you are that you won’t get fooled by an online scam, you can never be too careful when opening texts and …

In 2023, HBO Max and Discovery+ combined to form Max. As a result, the new releases on Max are more varied than ever, with HBO and …

Well, I guess someone sold the Titanfall rights to Netflix, based on the official trailer for Jennifer Lopez’s newest movie for the streamer. I kid, …

NASA’s Solar Dynamics Observatory (SDO) has captured footage of a rare quadruple solar flare eruption. The eruption began around 1 a.m. on Tuesday, April 23. …

The most important part of Reddit has been and likely always will be the comments section. In my short time on the social media service, …

If you own a Windows 11 computer, you are about to start seeing ads for apps that you haven’t downloaded in the Start menu. Thankfully, …

People really like their iPhones. But I think everyone can agree that we all get way too many notifications. Notifications are everywhere. If you install …