People are watching an insane amount of true crime content on Max
The runaway success on Max of the docuseries Quiet On Set: The Dark Side of Kids TV has underscored what appears to be a core …
The runaway success on Max of the docuseries Quiet On Set: The Dark Side of Kids TV has underscored what appears to be a core …

We’re only halfway through April, and we’re already getting another round of title additions (and subtractions) from Xbox Game Pass. However, with every new game …

When Michael Lindsay-Hogg was tapped to direct a making-of documentary to accompany work on The Beatles’ 1970 album Let It Be, he had no way …

The 2024 solar eclipse was a brilliant cosmic display. While I didn’t get to see the totality for myself (I was out of town at …
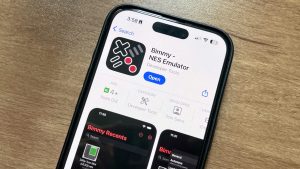
The first NES emulator for iPhone and iPad is now available on the App Store, following some recent App Review Guideline changes made by Apple. …

It’s been about a year and a half since the first season of Andor concluded, but the long wait for season 2 is finally coming …

It’s time for some indie games! We’re about two months out from Nintendo’s last Direct event, which the company hosted on February 21st, so it’s …

Insta360 once again pushes the envelope of 360-degree photography with the launch of its latest model, the Insta360 X4. As a very strong successor to …

watchOS 10.5 beta 2 is now available to Apple Watch users. After a mild update with watchOS 10.4, it seems this next version won’t bring …

tvOS 17.5 beta 2 is now available to everyone with an Apple TV that can run tvOS. At this moment, it’s unclear what this operating …

A week after seeding a new beta build of the first visionOS 1.2, Apple is now seeding its second testing version. Although it’s unclear what’s …

Apple has just released macOS 14.5 beta 2 to developers. At this moment, it’s unclear what features this software update might bring, as we haven’t …

A couple of weeks after releasing iOS 17.5 beta 1 to developers, Apple is now seeding beta 2. This might be Apple’s last iOS 17 update for …

There are Echo Dot deals all the time at Amazon. That is surely a big part of the reason why it’s the single best-selling Alexa …

I’ve been a fan of the Apple Vision Pro since even before Apple actually announced the spatial computer. I still am. I want that future …

Last year, when Apple announced its new Beats Studio Pro headphones, it came as something of a surprise. Hardcore fans already knew they were coming …

Apple always made beautiful leather accessories. More than that, it also helped create a profitable market of third-party leather accessories for iPhone, iPad, MacBook, Apple …

I’ve said that paying for premium artificial intelligence (AI) products is often worthwhile. It’s not just about access to premium features, improved privacy, and faster …
After the iPhone 15 release, we turn our attention to Apple’s upcoming iPhone 16. This new series is expected to be announced later in 2024. …

We found so many great daily deals for you to check out on Tuesday, like the Apple Watch Series 9 for just $329 instead of …

Today, KeyBudz is releasing its new HyperFoam Tips for AirPods Pro users, claiming it can offer “ultimate comfort” while taking advantage of AirPods crystal clear …

A few new reports say Apple might double the storage of the iPhone 16 Pro without raising prices. If true, Cupertino would offer both iPhone …

Amazon’s Blink home security camera brand is known in the industry for two main things. First, Blink wire-free cameras have the best battery life you …
Fans of foldable devices are probably waiting for Google to release the Pixel Fold 2 this summer. The device has appeared in various leaks, indicating …

If you are willing to download a few unfamiliar apps and watch some ads along the way, there’s more free (and legal) content to watch …

Spider-Man 4 has been the talk of the town for the past few months. And it hasn’t always been good news. If rumors are accurate, …

There is one, and only one, TV drama about a sexy, sociopathic female assassin that a streaming TV subscriber will ever need in their life. …

Late last year, YouTube finally began cracking down on ad blockers. The company encouraged users who blocked ads to upgrade to YouTube Premium and disabled …

Even though the first season of Tehran debuted on Apple TV+ back in 2020, anyone who dives into it for the first time today would …

Back in October of 2022, astronomers around the world were baffled and awed by the largest gamma-radiation burst we’ve ever recorded. The burst was so …

About a month ago, we began seeing PS5 Pro specs leaks that seemed to be genuine. Reports said that Sony was investigating the origin of …